 |
Adequacy Audit Methodology (print ref: Part 3, Section 2.1.3)
The methodology used for conducting an Adequacy Audit is a much-simplified version of a Functional or Vertical Compliance Audit (see Part 3 Section 3.2.1) and involves the following steps:
- The Auditor reads carefully through all of the documentation supplied
- While reading the documentation the Auditor checks that it addresses each of the areas identified in the Adequacy Audit Checklist of Annex E. This checklist is based on the Compliance Audit Checklists of Annexes F, G and H, but only uses the main headings of each, and not the detailed questions.
- The Auditor records the corresponding reference(s) to the organisation's documentation where the answer to each question on the checklist can be found. The second column on the checklist is used for recording this reference and should include the document title, section and/or page number.
- For each question on the checklist the Auditor records to what extent the documentation addresses the issue. It should be recalled that during an Adequacy Audit the Auditor is looking for the existence of broad systems and structures to address Data Protection issues and not the fine detail.
- The final column of the Adequacy Audit Checklist is used to record this assessment using one of three categories:
Assessment |
Enter |
Documentation addresses issue adequately |
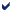 |
Documentation does not address issue adequately |
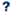 |
No reference can be found to the issue in the documentation |
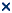 |
Return to top
|
|


![]()
![]()
![]()

